2023.06.07 - [클라우드/AWS] - [AWS] EKS Automation- 7주차 - ACK S3 생성
2023.06.07 - [클라우드/AWS] - [AWS] EKS Automation- 7주차 - ACK EC2, VPC생성
2023.06.07 - [클라우드/AWS] - [AWS] EKS Automation- 7주차 - ACK RDS생성
ACK를 사용하여 APIGateway를 생성하고 삭제해보도록하자. 내용은 위와 동일하다.
참조 : https://aws-controllers-k8s.github.io/community/docs/tutorials/apigatewayv2-reference-example/
Manage HTTP APIs with the ACK APIGatewayv2 Controller
Create and Invoke an Amazon APIGateway HTTP API using ACK APIGatewayv2 controller deployed on Amazon Elastic Kubernetes Service (EKS).
aws-controllers-k8s.github.io
ACK APIGateway2 Controller 설치 with Helm - Public-Repo Github
# helm pull
export SERVICE=apigatewayv2
export RELEASE_VERSION=`curl -sL https://api.github.com/repos/aws-controllers-k8s/$SERVICE-controller/releases/latest | grep '"tag_name":' | cut -d'"' -f4`
helm pull oci://public.ecr.aws/aws-controllers-k8s/$SERVICE-chart --version=$RELEASE_VERSION
tar xzvf $SERVICE-chart-$RELEASE_VERSION.tgz
# helm chart 확인
tree ~/$SERVICE-chart
# ACK APIGateway2 Controller 설치
export ACK_SYSTEM_NAMESPACE=ack-system
export AWS_REGION=ap-northeast-2
helm install --create-namespace --namespace $ACK_SYSTEM_NAMESPACE ack-$SERVICE-controller --set aws.region="$AWS_REGION" ~/$SERVICE-chart
# 설치 확인
helm list --namespace $ACK_SYSTEM_NAMESPACE
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
ack-apigatewayv2-controller ack-system 1 2022-04-25 00:11:34.950376704 +0900 KST deployed apigatewayv2-chart-v0.1.0 v0.1.0
kubectl -n ack-system get pods -l "app.kubernetes.io/instance=ack-apigatewayv2-controller"
NAME READY STATUS RESTARTS AGE
ack-apigatewayv2-controller-apigatewayv2-chart-747bf88db5-pw49l 1/1 Running 0 44s
kubectl get crd | grep apigatewayv2
apis.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
authorizers.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
deployments.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
integrations.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
routes.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
stages.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
vpclinks.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
IRSA 설정
# helm pull
export SERVICE=apigatewayv2
export RELEASE_VERSION=`curl -sL https://api.github.com/repos/aws-controllers-k8s/$SERVICE-controller/releases/latest | grep '"tag_name":' | cut -d'"' -f4`
helm pull oci://public.ecr.aws/aws-controllers-k8s/$SERVICE-chart --version=$RELEASE_VERSION
tar xzvf $SERVICE-chart-$RELEASE_VERSION.tgz
# helm chart 확인
tree ~/$SERVICE-chart
# ACK APIGateway2 Controller 설치
export ACK_SYSTEM_NAMESPACE=ack-system
export AWS_REGION=ap-northeast-2
helm install --create-namespace --namespace $ACK_SYSTEM_NAMESPACE ack-$SERVICE-controller --set aws.region="$AWS_REGION" ~/$SERVICE-chart
# 설치 확인
helm list --namespace $ACK_SYSTEM_NAMESPACE
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
ack-apigatewayv2-controller ack-system 1 2022-04-25 00:11:34.950376704 +0900 KST deployed apigatewayv2-chart-v0.1.0 v0.1.0
kubectl -n ack-system get pods -l "app.kubernetes.io/instance=ack-apigatewayv2-controller"
NAME READY STATUS RESTARTS AGE
ack-apigatewayv2-controller-apigatewayv2-chart-747bf88db5-pw49l 1/1 Running 0 44s
kubectl get crd | grep apigatewayv2
apis.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
authorizers.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
deployments.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
integrations.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
routes.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
stages.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
vpclinks.apigatewayv2.services.k8s.aws 2022-04-24T15:11:34Z
샘플배포
apiVersion: apps/v1
kind: Deployment
metadata:
name: echoserver
spec:
selector:
matchLabels:
app: echoserver
replicas: 1
template:
metadata:
labels:
app: echoserver
spec:
containers:
- image: gcr.io/google_containers/echoserver:1.4
imagePullPolicy: Always
name: echoserver
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: echoserver
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb-ip"
service.beta.kubernetes.io/aws-load-balancer-internal: "true"
spec:
ports:
- port: 80
targetPort: 8080
protocol: TCP
type: NodePort
selector:
app: echoserverauthor-deployment.yml
# 샘플 애플리케이션 배포 : 디플로이먼트와 서비스
kubectl apply -f https://github.com/aws-samples/amazon-apigateway-ingress-controller-blog/raw/Mainline/apigw-ingress-controller-blog/echoserver.yml
kubectl apply -f https://github.com/aws-samples/amazon-apigateway-ingress-controller-blog/raw/Mainline/apigw-ingress-controller-blog/author-deployment.yml
# 배포 확인
kubectl get deploy,svc
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/author-deployment 1/1 1 1 73m
deployment.apps/echoserver 1/1 1 1 73m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/authorservice ClusterIP 10.100.147.240 <none> 80/TCP 73m
service/echoserver NodePort 10.100.104.51 <none> 80:31534/TCP 73m
# NLB 도메인 주소 DNS 조회 : 내부 NLB 이므로 사설 IP가 출력된다
NLB1DNS=$(kubectl get svc authorservice -o jsonpath={.status.loadBalancer.ingress[0].hostname})
dig +short $NLB1DNS
192.168.4.234
NLB2DNS=$(kubectl get svc echoserver -o jsonpath={.status.loadBalancer.ingress[0].hostname})
dig +short $NLB2DNS
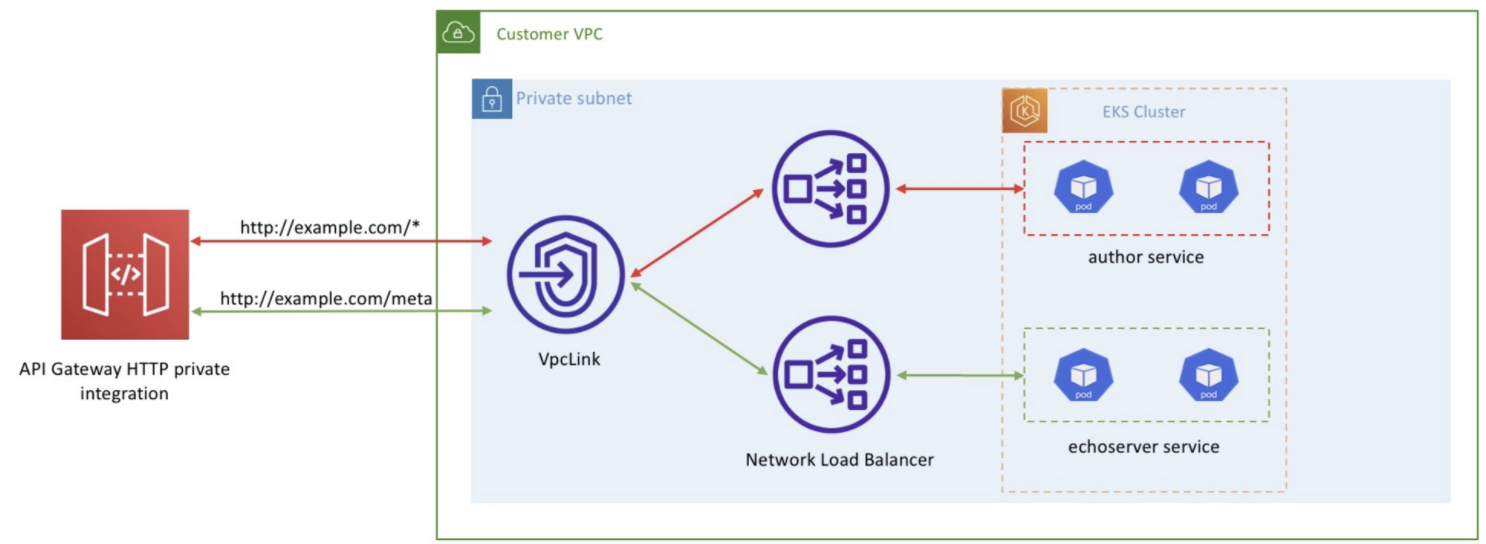
192.168.4.171VPC Link (내부 NLB) 를 사용하는 API Gateway (HTTP API) 생성 및 호출 확인 - 링크
Integrate Amazon API Gateway with Amazon EKS | Amazon Web Services
Since 2015, customers have been using Amazon API Gateway to provide scalable and secure entry points for their API services. As customers adopt Amazon Elastic Kubernetes Service (Amazon EKS) to orchestrate their services, they have asked us how they can us
aws.amazon.com
# VPC Link 가 사용할 보안그룹 생성 : Create security group for the VPC link
VPC_ID=$(aws ec2 describe-vpcs --query 'Vpcs[0].VpcId' --output text)
VPCLINK_SG=$(aws ec2 create-security-group \
--description "SG for VPC Link" \
--group-name SG_VPC_LINK \
--vpc-id $VPC_ID \
--region $AWS_REGION \
--output text \
--query 'GroupId')
# VPC Link 생성 : Create a VPC Link for the internal NLB
# 아래 서브넷 ID는 Private Subnet 을 지정
cat > vpclink.yaml<<EOF
apiVersion: apigatewayv2.services.k8s.aws/v1alpha1
kind: VPCLink
metadata:
name: nlb-internal
spec:
name: nlb-internal
securityGroupIDs:
- $VPCLINK_SG
subnetIDs:
- $(aws ec2 describe-subnets \
--filter Name=tag:kubernetes.io/role/internal-elb,Values=1 \
--query 'Subnets[0].SubnetId' \
--region $AWS_REGION --output text)
- $(aws ec2 describe-subnets \
--filter Name=tag:kubernetes.io/role/internal-elb,Values=1 \
--query 'Subnets[1].SubnetId' \
--region $AWS_REGION --output text)
EOF
kubectl apply -f vpclink.yaml
# VPC Link 생성 확인
kubectl describe vpclink nlb-internal | grep 'Vpc Link'
Vpc Link ID: YYYYYYYYY
Vpc Link Status: AVAILABLE
Vpc Link Status Message: VPC link is ready to route traffic
Vpc Link Version: V2
aws apigatewayv2 get-vpc-links | jq
# API GW 생성 (VPC Link 연동) : route($default >> authorservice), route(/meta, GET >> echoserver)
cat > apigw-api.yaml<<EOF
apiVersion: apigatewayv2.services.k8s.aws/v1alpha1
kind: API
metadata:
name: apitest-private-nlb
spec:
body: '{
"openapi": "3.0.1",
"info": {
"title": "ack-apigwv2-import-test-private-nlb",
"version": "v1"
},
"paths": {
"/\$default": {
"x-amazon-apigateway-any-method" : {
"isDefaultRoute" : true,
"x-amazon-apigateway-integration" : {
"payloadFormatVersion" : "1.0",
"connectionId" : "$(kubectl get vpclinks.apigatewayv2.services.k8s.aws \
nlb-internal \
-o jsonpath="{.status.vpcLinkID}")",
"type" : "http_proxy",
"httpMethod" : "GET",
"uri" : "$(aws elbv2 describe-listeners \
--load-balancer-arn $(aws elbv2 describe-load-balancers \
--region $AWS_REGION \
--query "LoadBalancers[?contains(DNSName, '$(kubectl get service authorservice \
-o jsonpath="{.status.loadBalancer.ingress[].hostname}")')].LoadBalancerArn" \
--output text) \
--region $AWS_REGION \
--query "Listeners[0].ListenerArn" \
--output text)",
"connectionType" : "VPC_LINK"
}
}
},
"/meta": {
"get": {
"x-amazon-apigateway-integration": {
"uri" : "$(aws elbv2 describe-listeners \
--load-balancer-arn $(aws elbv2 describe-load-balancers \
--region $AWS_REGION \
--query "LoadBalancers[?contains(DNSName, '$(kubectl get service echoserver \
-o jsonpath="{.status.loadBalancer.ingress[].hostname}")')].LoadBalancerArn" \
--output text) \
--region $AWS_REGION \
--query "Listeners[0].ListenerArn" \
--output text)",
"httpMethod": "GET",
"connectionId": "$(kubectl get vpclinks.apigatewayv2.services.k8s.aws \
nlb-internal \
-o jsonpath="{.status.vpcLinkID}")",
"type": "HTTP_PROXY",
"connectionType": "VPC_LINK",
"payloadFormatVersion": "1.0"
}
}
}
},
"components": {}
}'
EOF
kubectl apply -f apigw-api.yaml
# stage 생성
echo "
apiVersion: apigatewayv2.services.k8s.aws/v1alpha1
kind: Stage
metadata:
name: "apiv1"
spec:
apiID: $(kubectl get apis.apigatewayv2.services.k8s.aws apitest-private-nlb -o=jsonpath='{.status.apiID}')
stageName: api
autoDeploy: true
" | kubectl apply -f -
# stage URL 호출 정보 확인
kubectl get api apitest-private-nlb -o jsonpath={.status.apiEndpoint}
https://p7yum26d9i.execute-api.ap-northeast-2.amazonaws.com
# Invoke the authorservice service
curl -s $(kubectl get api apitest-private-nlb -o jsonpath="{.status.apiEndpoint}")/api/author/ | head
{
"authors": [
{
"author": "Peter Sbarski",
"id": "Peter-Sbarski",
"books": "9781617293825",
"about": ""
},
...(생략)...
# Invoke the echoserver service by invoking the meta path
curl -s $(kubectl get api apitest-private-nlb -o jsonpath="{.status.apiEndpoint}")/api/meta | head
CLIENT VALUES:
client_address=192.168.4.171
command=GET
real path=/api/meta
query=nil
request_version=1.1
request_uri=http://p7yum26d9i.execute-api.ap-northeast-2.amazonaws.com:8080/api/meta
...(생략)...
# 파드에서 접속 로그 확인 : 맨 왼쪽 IP 는 NLB 의 IP 입니다
kubectl logs -l app=author --since=1h
192.168.4.234 - - [24/Apr/2022:17:11:09 +0000] "GET /api/author/ HTTP/1.1" 200 3015 "-" "curl/7.79.1" "-"
192.168.4.234 - - [24/Apr/2022:17:11:21 +0000] "GET /api/author/ HTTP/1.1" 200 3015 "-" "curl/7.79.1" "-"
...
kubectl logs -l app=echoserver --since=1h
192.168.4.171 - - [24/Apr/2022:17:12:48 +0000] "GET /api/meta HTTP/1.1" 200 734 "-" "curl/7.79.1"
192.168.4.171 - - [24/Apr/2022:17:14:08 +0000] "GET /api/meta HTTP/1.1" 200 734 "-" "curl/7.79.1"
...
삭제
# API GW 와 NLB 관련 리소스 삭제
kubectl delete stages.apigatewayv2.services.k8s.aws apiv1
kubectl delete apis.apigatewayv2.services.k8s.aws apitest-private-nlb
kubectl delete vpclinks.apigatewayv2.services.k8s.aws nlb-internal
kubectl delete service echoserver # NLB 삭제
kubectl delete services authorservice # NLB 삭제
sleep 10 # 10초 정도 후 아래 VPC Link 삭제 진행
# VPC Link 가 사용했던 보안그룹 삭제
aws ec2 delete-security-group --group-id $VPCLINK_SG --region $AWS_REGION
# ACK APIGateway2 Controller 삭제
# ACK APIGateway2 Controller 관련 helm uninstall
export SERVICE=apigatewayv2
helm uninstall -n $ACK_SYSTEM_NAMESPACE ack-$SERVICE-controller
# ACK APIGateway2 Controller 관련 crd 삭제
kubectl delete -f ~/$SERVICE-chart/crds/
# ACK APIGateway2 Controller 관련 namespace 삭제
kubectl delete namespace $ACK_K8S_NAMESPACE
# AWS IAM Role 삭제 : ack-apigatewayv2-controller
# AWS Load Balancer controller 삭제
# AWS Load Balancer controller 관련 helm uninstall
helm uninstall -n kube-system aws-load-balancer-controller
# AWS IAM Role 삭제
eksctl delete iamserviceaccount --cluster=$CLUSTER_NAME --namespace=kube-system --name=aws-load-balancer-controller'클라우드 > AWS' 카테고리의 다른 글
| [AWS] EKS 웹콘솔 생성 시 문제 (0) | 2024.06.19 |
|---|---|
| [AWS] EKS Automation- 7주차 - FLUX (0) | 2023.06.07 |
| [AWS] EKS Automation- 7주차 - ACK RDS생성 (0) | 2023.06.07 |
| [AWS] EKS Automation- 7주차 - ACK EC2, VPC생성 (0) | 2023.06.07 |
| [AWS] EKS Automation- 7주차 - ACK S3 생성 (0) | 2023.06.07 |



